Platform Engineering with Microsoft CAF Terraform Super Module
Effective infrastructure management is critical for organizations aiming to achieve agility and efficiency in today’s digital challenges.
Platform engineering, combined with robust cloud solutions, offers the tools and frameworks necessary to streamline operations and accelerate innovation.
In this blog post, we will delve into the Microsoft CAF Terraform Super Module, examining its role in addressing platform engineering challenges and providing a practical guide to get you started with this powerful toolset.
Introduction
What is Platform Engineering?
Platform engineering is a practice focused on designing and building toolchains and workflows that enable self-service capabilities for software engineering teams. This discipline aims to provide a frictionless developer experience by creating platforms that abstract the complexities of infrastructure management, allowing developers to focus on coding and delivering features. Platform engineering helps you centralize and scale specialized knowledge across the entirety of development and operations lifecycles by reducing or eliminating cognitive load and manual steps.
Platform engineering can broken down in three categories:
- Underlying platforms: This is where your platform(s) will run, including the build of the underlying platform(s), maintaining the platform(s), securing the platform(s), and automating the platform(s).
- Platform capabilities: Referring to what your platform(s) can do for the engineers using it, and what the engineers can do on the platform(s) you built.
- Platform interaction: This is how engineers will use the platform(s) you build, including build methods for engineers to interact with your platform(s). This could either be a CLI, API, or user-interface. Whatever the method, you’ll have to give engineers a way to work with the platform(s) you build.
The ultimate goal of platform engineering is to improve productivity, consistency, and reliability across the software development lifecycle by automating repetitive tasks and providing standardized environments.
What is the Terraform CAF Super Module?
The Terraform Cloud Adoption Framework (CAF) Super Module is a comprehensive, modular solution designed to streamline the deployment and management of resources on Microsoft Azure. It encapsulates best practices, guidelines, and enterprise-scale architecture principles from the Microsoft Cloud Adoption Framework for Azure, providing a cohesive and scalable approach to cloud adoption.
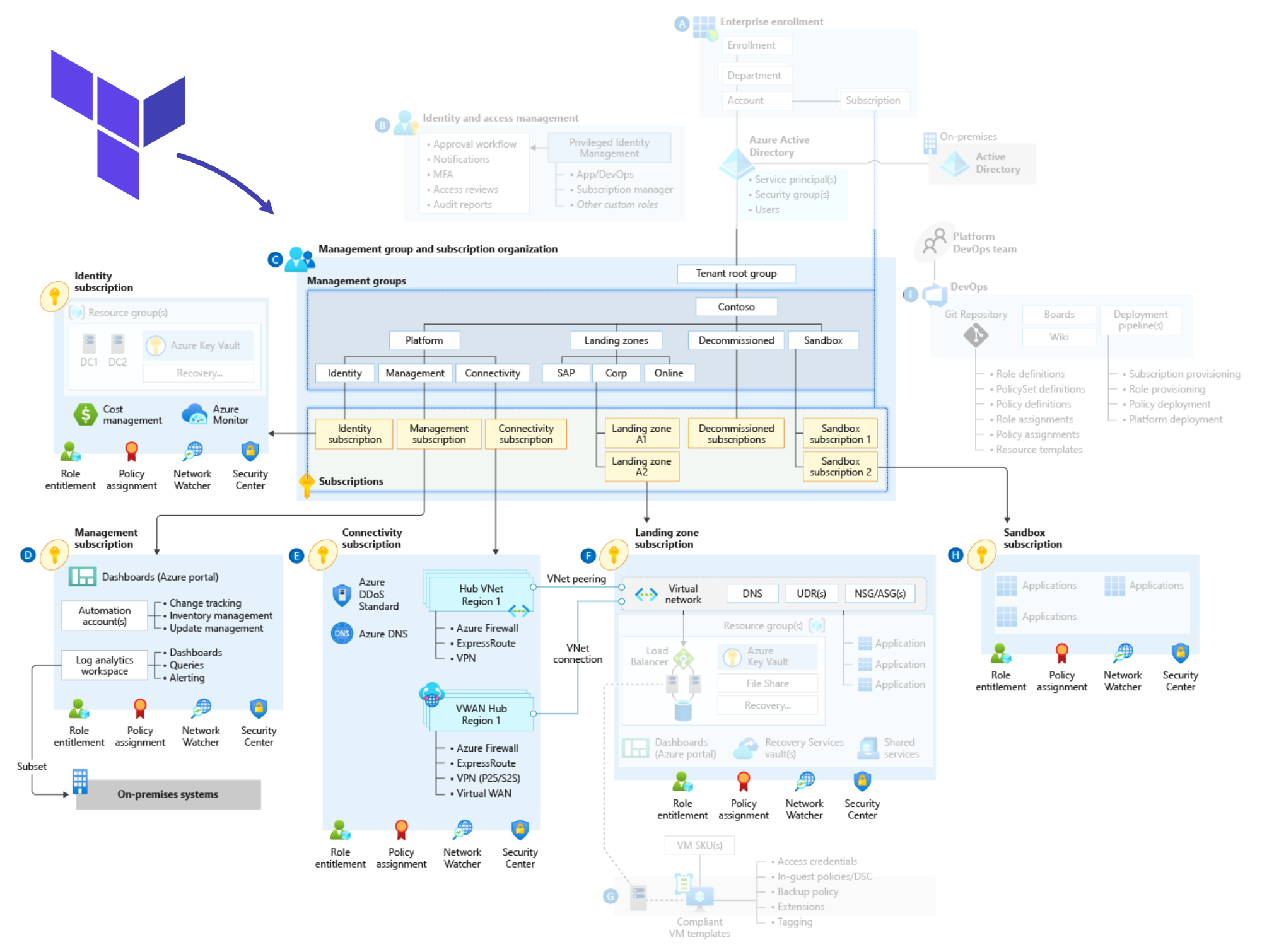
The CAF Super Module is a collection of Terraform modules, templates, and configurations that simplify the provisioning of complex cloud environments. It includes predefined modules for various Azure services, such as virtual networks, storage accounts, and virtual machines, and provides a consistent way to manage these resources through infrastructure as code (IaC). The key features of the Terraform CAF Super Module include:
- Modularity: Components can be used independently or together, allowing for flexible and customizable cloud architectures.
- Best Practices: Embeds Azure’s best practices for security, governance, and compliance, ensuring robust and secure deployments.
- Scalability: Supports both small and large-scale deployments, making it suitable for enterprises of any size.
- Automation: Automates the deployment and configuration of Azure resources, reducing the time and effort required for cloud infrastructure management.
Platform engineering teams often face several challenges, including complexity in managing multi-cloud environments, consistency in deployments, security and compliance, and resource optimization. The CAF Super Module simplifies the management of Azure environments by providing standardized modules that handle the complexities of Azure infrastructure. By using predefined templates and configurations, the CAF Super Module ensures consistent and repeatable deployments across different environments.The Super Module incorporates Azure best practices for security and compliance, helping to enforce organizational policies and standards automatically. It provides tools for monitoring and optimizing resource usage, ensuring efficient utilization of cloud resources.
One of the core principles of platform engineering is to democratize access to cloud resources, enabling development teams to autonomously manage their environments while adhering to organizational standards. The Terraform CAF Super Module plays a crucial role in achieving this by self-service capabilities, governance and control, automation and scalability. The CAF Super Module provides developers with easy-to-use modules and templates, allowing them to provision and manage Azure resources without deep expertise in cloud infrastructure. It ensures that all deployments comply with corporate policies and governance standards, reducing the risk of misconfigurations and security breaches. The Terraform CAF Super Module automates routine tasks and processes, freeing up platform engineering teams to focus on more strategic initiatives. Through this it supports the growth of cloud environments by providing scalable and repeatable deployment patterns, ensuring that infrastructure can grow alongside the organization.
Getting started with the Terraform CAF Super Module
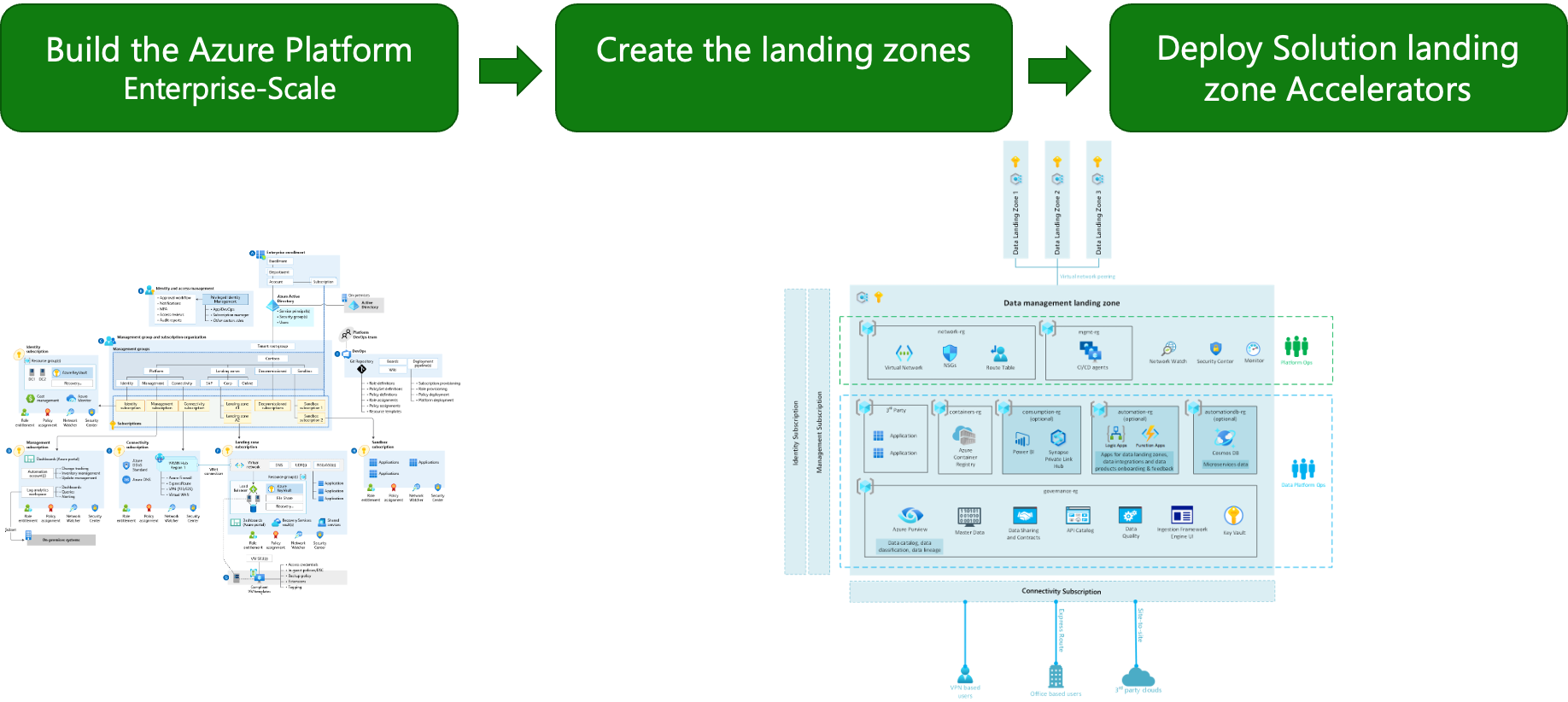
Let’s get started with building Azure Platform Landing zones with the Terraform CAF Super Module. We’ll cover on how to deploy the platform landing zones, including:
- Azure Remote State management
- Azure landing zones for management groups, policy definitions, policy assignments and RBAC
- Identity services
- Monitoring services
- Connectivity services
Prerequisites
Before diving into the deployment process, ensure you have the following prerequisites in place:
- Azure Tenant with Owner Permissions: You must have access to an Azure tenant with Global Administrator privileges, and have Management Group Contributor permissions on a branch or root management group.
- Active Azure Subscription with Owner Permissions: You must have one ore more active Azure subscriptions, where you’ll have Owner privileges. You are required to have a deep understanding of Azure services. It is assumed that you already have deep knowledge of the CAF.
- Azure CLI: Install Azure CLI for interacting with Azure services from the command line. You can install Azure CLI by following the instructions at Microsoft’s official documentation.
- Git: You’ll need to have Git installed on your machine to track and deploy changes to your files within the source code of your app. We’ll be assuming you have basic knowledge of Git.
- GitHub: A GitHub account is necessary to host the configuration files in a private (GitHub) repository.
- Terraform: You’ll need to have advanced knowledge of Terraform.
- Visual Studio Code: Visual Studio Code is needed as an integrated development environment (IDE) for editing configuration files and managing the repository.
Initial setup
Step 1: Create a private repository in your current GitHub organization. Other tools or platforms can be used as well. However, it has to be a git repository.
Step 2: Clone the platform starter repository. This is an empty environment that gets you started with your initial configuration files and create a coherent stack. If you are using it from GitHub, you can directly select “Use this template”. You can also use the command below:
# Adjust the name of your organization and repository
git clone git://github.com/<org>/<repo> contoso && cd contosoStep 3: Open Visual Studio Code from the contoso folder and make sure you trust the repository. Once opened, it should display the following structure:
Step 4: Install the VS Code Remote Development extension pack. This includes the Remote - SSH, Dev Containers, WSL, and Remote - Tunnels extensions. Once installed, re-open vscode in the dev container by clicking on the green bottom left button from the menu, and select the Reopen in Container option. You should then see a terminal where you will run all commands in the following section of this blog article.
Step 5: The configuration folder is now ready to use. Let’s clone the logic of landing zones (the Terraform code) that we will use to run the commands. Make sure you do not use another name as landingzones, as the framework assumes the landingzones Terraform is cloned in a repository called this way. Run the command below in your terminal.
git clone https://github.com/Azure/caf-terraform-landingzones.git landingzonesStep 6: New features within the framework are released on regular basis. To use them you need to make sure the Terraform code is also using the correct branch or tag. Check the latest tag from the landingzones repo here, and run the command below to checkout to the latest tag:
# Adjust the tag to the latest release
git checkout <tag>Deployment
Going forward, you should choose your deployment mode to continue. At the time of writing this blog, the following scenario’s are available:
- Single subscription lab
- Multi subscriptions (reuse existing subscriptions)
- Multi subscriptions (creating new subscriptions with EA/MCA)
For the purpose of this guide, we’ll go with the first option.
Step 7: Login to your Azure environment by using the rover login command in your terminal. Click on the URL https://microsoft.com/devicelogin, set the code and authenticate with your Azure account.
Step 8: Now we’re going to pick the right configuration files example from the landing zones and put it in our configuration repository, by running the command below:
'/tf/caf/landingzones/templates/platform/deploy_platform.sh'You’ll be prompted to answer a couple of questions. After, the definition files are generated. These will be a set of YAML files.
Step 9: You’ll now have to follow the readme.md located in your repository /tf/caf/platform/definition/GETTING-STARTED.md, and follow the instructions. The first step to generate the Terraform configuration files and customized readme with rover ignite is to run the command below:
ansible-playbook /tf/caf/landingzones/templates/ansible/ansible.yaml \
--extra-vars "@/tf/caf/platform/definition/ignite.yaml"Step 10: Next, go to the /tf/caf/configuration/contoso/platform/level0/launchpad/readme.md file, and follow the instructions to deploy the launchpad (level 0).
You’ve taken the first crucial step toward simplifying and automating your Azure infrastructure management. To continue building and scaling your environment, refer to the readme.md file for detailed instructions on deploying subsequent levels. Once level 0 is completed, you can carry on with level 1: management, identity, then alz. Once level 1 is completed, level 2 azure subscription vending machine (asvm) and identity can be deployed, alongside with connectivity components stating with virtual WAN. By following these steps, you will harness the full potential of the CAF Super Module, ensuring a robust, secure, and scalable Azure deployment. To learn more about the levels hierarchy, please read this article.
Closing words
With this foundation, you are well on your way to optimizing your cloud strategy and empowering your development teams through platform engineering excellence. Platform engineering is essential for modern software development, and the Terraform CAF Super Module provides a powerful toolset to address the complexities of managing Azure environments. By leveraging this module, organizations can enhance their cloud adoption strategies, ensure consistent and secure deployments, and empower their development teams with self-service capabilities.
To learn more about the material we’ve covered in this blog article, you can start with reading some of the resources below:
Thank you for taking the time to go through this post and making it to the end. Stay tuned, because we’ll keep continuing providing more content on topics like this in the future.
Author: Rolf Schutten
Posted on: June 30, 2024