Choosing between Azure Firewall and Network Security Groups
A much-discussed topic is the difference between an Azure Firewall and Azure Network Security Groups (NSG), particularly why one is chosen over the other in specific situations.
In this article, I’ll explain what these services are, what their differences are, which considerations lead to a choice between these services, and how they can be used together to enable zero trust.
What is Azure Firewall?
An Azure Firewall is a cloud-native and intelligent network firewall security service that protects cloud workloads running in Azure against threats. It provides traffic controls of both east-west traffic (between or within data centers) and north-south traffic (flowing in and out of a data center). Azure Firewall is a stateful firewall, with built-in high availability and unlimited scalability.
Azure Firewall is designed to analyze and filter layer 3, layer 4, and layer 7 traffic. Unlike network security groups, Azure Firewall supports threat-based filtering. In addition, Azure Firewall also supports FQDN (fully qualified domain name) tags, which application rules use to route required outgoing traffic through the firewall.
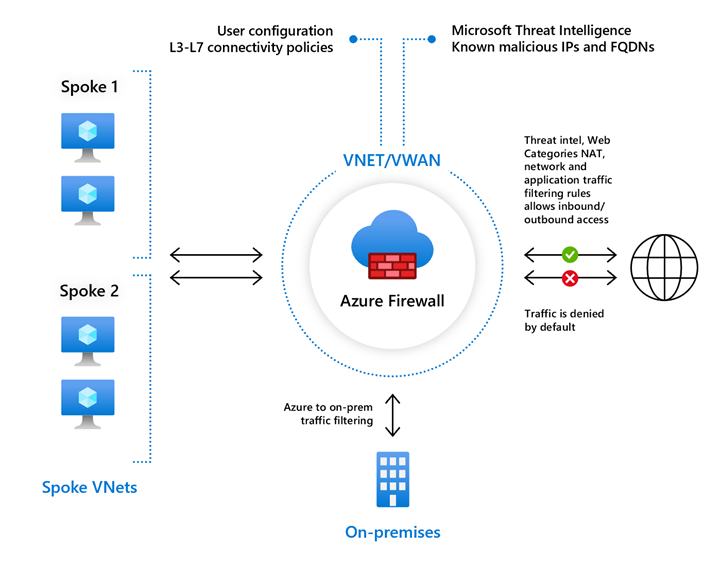
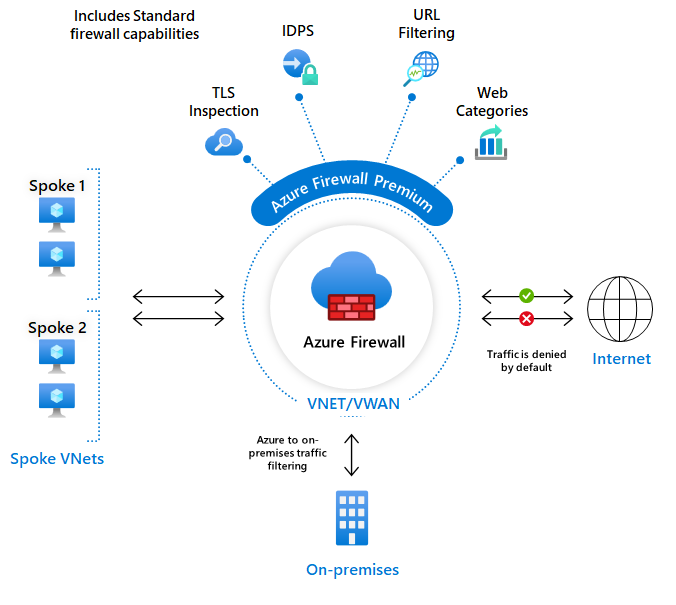
Azure Firewall Premium
In addition to the features that an Azure Firewall Standard offers, Azure Firewall Premium gives you access to more advanced capabilities for IDPS (Intrusion Detection and Prevention System) based on signatures. It enables you to continuously search for specific patterns to detect attacks.
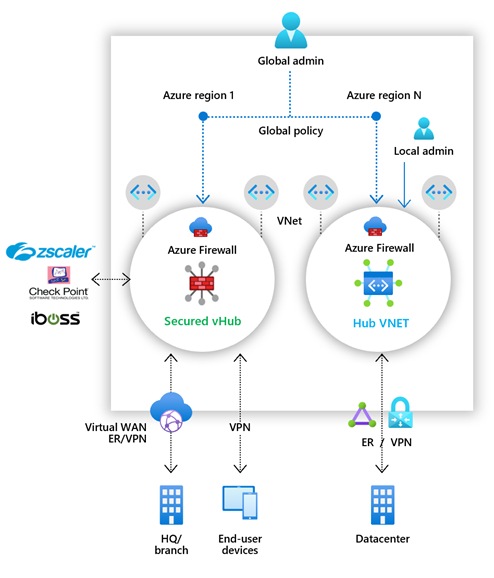
Azure Firewall Manager
You can use Azure Firewall Manager to manage multiple Azure Firewalls in a centralized way, even if they exist in more than one subscription. It uses firewall policies to apply network and application rules and configurations to the firewalls in your tenant.
Firewall Manager supports firewalls in both VNet (virtual network) and Secure Virtual Hub (VPN) environments. Secure virtual hubs use the Virtual WAN Route Automation solution to simplify routing traffic to the firewall with a few clicks.
What are Network Security Groups?
Network security groups are used to filter network traffic to and from Azure resources in an Azure virtual network. They contain security rules for allowing or denying inbound network traffic to or outbound network traffic from various types of Azure resources. These security rules are evaluated for priority and contain the 5 tuple details (source, source port, destination, destination port, and protocol) for allowing or denying the traffic. Therefore, no security rules should exist with the same priority and direction.
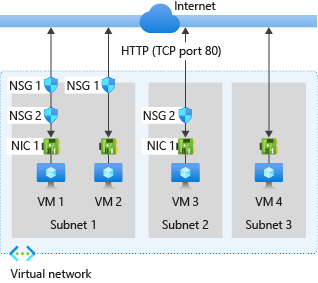
Azure creates default rules in every network security group you create. The priority of these rules cannot be adjusted, but the priority level is such that there is more than enough room to “overrule” these rules. These default rules can be found on Microsoft Docs.
If you want to learn more about network security group provisioning and deployment, I recommend checking out one of my previous articles about Getting started with Azure Network Security Groups.
Choosing one over the other
Segmenting and filtering network traffic is always recommended, on any network. It makes sense to provide every network and its subnets with network security groups by default, except where this is not compatible (for example, in a subnet of an Azure Firewall, Gateway, or Azure Bastion). A network security group is free to use and significantly increases the security level. You should always use network security groups.
Azure Firewall provides several security features by default like basic traffic monitoring, access control lists, etc. If you need to filter traffic to (or even within) a VNET with threat-based filtering capabilities, you use Azure Firewall. If you need support for application FQDN tags, you use Azure Firewall. If you require to mask source and destination network addresses, you use Azure Firewall. If you want to filter traffic on the transport or application layer, you use Azure Firewall.
What about third-party firewalls?
An often asked question is why someone chooses Azure Firewall rather than third-party NVAs (Network Virtual Appliances) from vendors such as CheckPoint, Palo Alto, or Fortinet.
A third-party NVA is an IaaS implementation, consisting of a virtual machine with a custom image from the vendor. The throughput depends on the size of the VM. Azure Firewall is a managed service that runs as active/active and scales automatically depending on the traffic flow. Azure Firewall is fully managed through Azure Resource Manager and supports your configuration in Azure Firewall to make changes and updates to the environment using the same code structure/framework. As a result, the deployment is less complex compared to third-party NVAs. In addition, Azure Firewall provides managed service tags for various Azure services, making it easy to update rules to approve/deny traffic to native Azure services. Like many firewall vendors, Azure Firewall has the logic of several built-in rule engines and threat intelligence. Microsoft’s equivalent is the Intelligent Security API. This can be leveraged if other support services are used, such as Azure Monitor and Sentinel for SIEM/SOC. Third-party NVAs cannot do this or less, making the choice for Azure Firewall more logical, because you can build on existing knowledge to build dashboard and monitoring points.
Are third-party firewalls bad?
No. If you have a hybrid environment where existing firewalls exist based on vendor choice, then there is an existing set of rules for your whole environment. Linking an NVA from the same firewall supplier is very easy and straightforward, so it makes sense to reuse it in Azure. It makes the network and security operations easier if the situation of having a hybrid environment is going to persist for a while. While Azure Firewall offers many benefits, having multiple firewall providers makes troubleshooting difficult and inefficient as rulesets must be updated in several places.
Why is Azure Firewall so expensive?
It’s really not. If after reading this article you still think that you are not getting your money’s worth with Azure Firewall, then Azure Firewall is not for you. Find a solution or service that meets your requirements, and if that leads you to Azure Firewall, then the alternatives are not cheaper. To lower costs there are allocation and de-allocation methods available, which can be used through Azure PowerShell to stop Firewall billing and start again when you map or unmap the firewall as per your requirements.
Combine Azure Firewall and Network Security Groups
Azure offers excellent security by default with encryption at rest (server-side encryption), traffic flow filtering (network security groups), et cetera. However, this is often not enough for modern business needs. Businesses use constant internet connectivity, hence firewall cloud security.
Azure Firewall and network security groups work together to reach zero trust and deep network security. Together, they provide multiple layers of defense. If one layer fails, the other layer can stand in its place.

Conclusion
In this article, you have read what Azure Firewall is, what network security groups are, what the differences are and how they can reinforce each other. Ultimately, a company’s network and security requirements lead to the right design and solution, and so it’s safe to say there could never be a choice between Azure Firewall or network security groups. Instead, the two reinforce each other. Network security groups are a hygiene factor and an Azure Firewall or third-party NVA is a must for any self-respecting company that is careful with its data.
Author: Rolf Schutten
Posted on: March 11, 2022