Extended Security Updates enabled by Azure Arc for Windows Server 2012/R2
In this blog, we’ll explore the significance of Microsoft’s Extended Security Updates program and the capabilities of Azure Arc, focusing on how these two combine to enhance your server security and management.
Introduction
Windows Server 2012 and 2012 R2, while reliable, have reached the end of their extended support on October 10, 2023. In response, Microsoft offers an innovative solution through its Extended Security Updates program that can be enabled by Azure Arc.
Maintaining an unsupported operating system can expose your organization to increased security risks, compliance violations, and limited access to new features. Extended Security Updates enable you to safeguard your systems and data while you plan your migration to newer server versions or explore cloud-based solutions. Microsoft’s Extended Security Updates program is a lifeline for organizations that still rely on Windows Server 2012 and 2012 R2. This program offers extended security updates beyond the end-of-support date, providing critical security patches and updates to keep your systems protected. With Extended Security Updates (ESUs), you can continue using Windows Server 2012 and 2012 R2 without fear of security vulnerabilities or compliance issues. This program essentially bridges the gap between your legacy systems and modern server infrastructure, ensuring you remain secure and compliant.
During Inspire 2023, Microsoft announced the possibility to purchase and seamlessly deploy ESUs through Azure Arc in on-premises or multicloud environments, right from the Azure portal. This is a great addition to the additional Azure services through Azure Arc, that help better secure, monitor, and govern end-of-support servers in tandem with your ESUs.
Extended Security Updates through Azure Arc
As Windows Server 2012 and Windows Server 2012 R2 approach the end of their support lifecycle on October 10, 2023, Azure Arc-enabled servers offer you the capability to enroll your current Windows Server 2012/2012 R2 machines in Extended Security Updates (ESUs). This approach not only provides cost-effective flexibility but also enhances the overall deployment experience, empowering you to seamlessly transition to Azure. The table below shows the different ESU enrollment methods.
| ESU for on-premises VMs | ESU for Arc-enabled VMs | ESU for Azure VMs | |
|---|---|---|---|
| Licensing | Volume Licensing Programs via your Microsoft representative. | Physical cores-based, and virtual cores-based licensing via the Azure portal. | Automatically enabled (may need additional configurations for other Azure products). |
| Pricing | Annually (Year 1 at 75%, Year 2 at 100%, and Year 3 at 125% of full license price). | Pay-as-you-Go subscription model | Free of charge (including other Azure products such as Azure Dedicated Host, Azure VMware Solution, Azure Nutanix Solution, and Azure Stack (Hub, Edge, and HCI). |
| Additional benefits | Free access to Azure Update Manager, Azure Automation Track Changes and Inventory, and Azure Policy Guest Configuration. | Additional year of extended security updates, only on Azure. |
Licensing
First of all, it’s important that you verify that your Windows Server licenses are equipped with Software Assurance, procured as subscription licenses, or are appropriately addressing Windows Server workloads hosted on servers under the purview of authorized Mobility Partners with license-inclusive offerings. In order to purchase ESUs, you must have Software Assurance through Volume Licensing Programs such as an Enterprise Agreement (EA), Enterprise Agreement Subscription (EAS), Enrollment for Education Solutions (EES), or Server and Cloud Enrollment (SCE). Alternatively, if your Windows Server 2012/2012 R2 machines are licensed through SPLA or with a Server Subscription, Software Assurance is not required to purchase ESUs. You can learn more about the Extended Security Updates requirements on the official Microsoft website.
When provisioning WS2012 ESU licenses through Azure Arc, you need to specify either virtual core or physical core license, and whether you are using Standard or Datacenter licenses. You’ll also need to attest to the number of associated cores (broken down by the number of 2-core and 16-core packs).
In the case of selecting a licensing model based on physical cores, a minimum of 16 physical cores per license is required. Most organizations opt for this physical core licensing model and choose either the Standard or Datacenter edition to align with their initial Windows Server licensing. While the Standard license permits usage on up to two virtual machines (VMs), the Datacenter license has no VM limit. The decision between Standard and Datacenter licensing should be influenced by the number of VMs you need to cover; in some cases, opting for the Datacenter license may be more cost-effective than the Standard license.
When opting for a licensing approach based on virtual cores, it’s essential to note that a minimum of eight virtual cores per Virtual Machine is a required. This virtual core-based licensing model is typically recommended when the VM operates on a third-party host or hyperscaler, such as AWS, GCP, or OCI, or when the Windows Server was originally licensed using a virtualization-based model. Most organizations tend to choose the Standard edition for their virtual core-based licenses. It’s crucial to be aware that customers who opt for virtual core licensing will consistently be billed at the Standard edition rate, even if the actual operating system in use is the Datacenter edition. It’s worth noting that virtual core licensing is not applicable to physical servers.
Each WS2012 ESU license can cover up to and including 10.000 cores. If you need ESUs for more than 10.000 cores, split the total number of cores across multiple licenses. How you structure the licenses and number of cores is completely up to you.
Pricing
In addition to providing a centralized management of security patching, ESUs enabled by Azure Arc gives you more flexibility with a pay-as-you-go subscription model, compared to the classic ESU offered through the Volume Licensing Center which are purchased in yearly increments. Obviously, the total cost will depend on your SKU’s and total number of cores. You can learn more about the Extended Security Updates pricing for Arc-enabled Windows Server 2012 virtual machines on the official Microsoft website.
Additional benefits
For Azure Arc-enabled servers that have been enrolled in WS2012 ESUs, free access will be granted to a range of Azure services commencing, like:
- Azure Update Manager: Offering unified management and governance of update compliance, extending its purview to encompass not just Azure and hybrid machines but also ESU update compliance for all Windows Server 2012/2012 R2 systems in your infrastructure.
- Azure Automation Change Tracking and Inventory: Keep tabs on changes within virtual machines hosted across Azure, on-premises, and various other cloud environments.
- Azure Policy Guest Configuration: Audit and verify configuration settings within virtual machines. Guest configuration extends support to Azure VMs as well as non-Azure physical and virtual servers via Azure Arc-enabled servers.
Moreover, additional Azure services are accessible through Azure Arc-enabled servers, offering capabilities such as:
- Microsoft Defender for Cloud: A component of the cloud security posture management (CSPM) domain, that provides server protection through Microsoft Defender for Servers. Its primary objective is to shield your infrastructure from diverse cyber threats and vulnerabilities.
- Microsoft Sentinel: This service collects and correlates security-related events, enabling a comprehensive analysis with data from other sources.
Deploy Extended Security Updates through Azure Arc
In this step-by-step guide, we’ll take you through the process of enabling Extended Security Updates via Azure Arc, using the Azure Portal. The demonstration environment starts with a standard, out-of-the-box Windows Server 2012 R2 installation. With this guide, you’ll gain insights into how Azure Arc can seamlessly integrate with your legacy infrastructure, providing an efficient path to ensure your servers remain secure and up to date. Let’s get started to enhance the longevity of your Windows Server 2012 R2 installation while harnessing the power of Azure Arc.
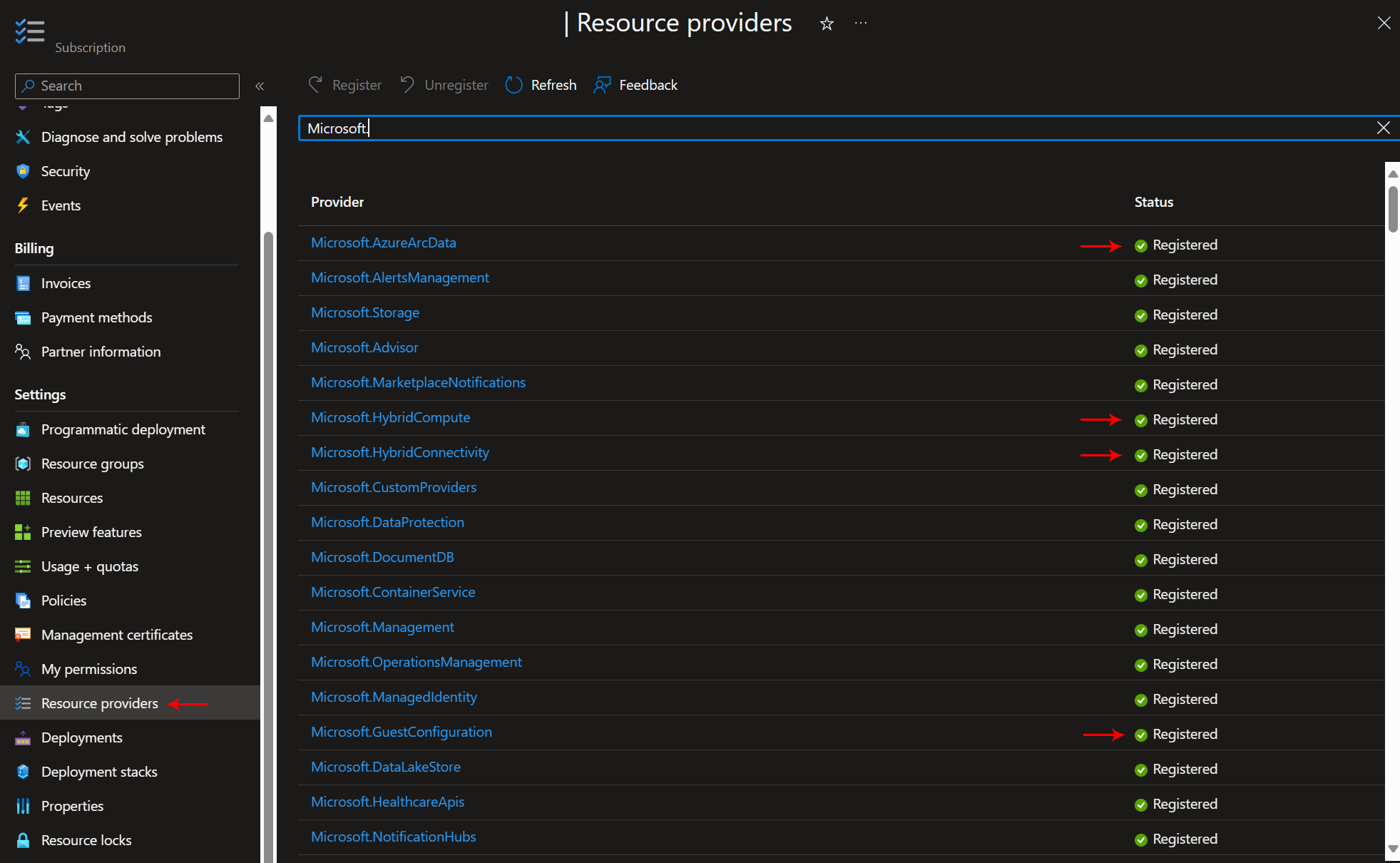
Step 1: Open a web browser and navigate to the Azure Portal. Log in with your Azure account credentials. First, we’ll need to register the necessary resource providers. In the Azure Portal, click on the “Subscriptions” option in the left-hand menu to view a list of your Azure subscriptions. Choose the specific Azure subscription where you want to register the Azure providers, which will contain your Azure Arc-enabled VMs. Click on the subscription you wish to configure. In the subscription’s menu, navigate to the “Resource providers” section. You can find this under “Settings” as shown in the screenshot below. Within the “Resource providers” section, you can see a list of available providers. Search for and select the following providers one by one:
- Microsoft.AzureArcData
- Microsoft.HybridCompute
- Microsoft.HybridConnectivity
- Microsoft.GuestConfiguration
After selecting each provider, click the “Register” button to start the registration process. The Azure Portal will display the status of provider registration. Wait for each provider’s status to change to “Registered”. This may take a few minutes. Once all selected providers show a status of “Registered,” you have successfully registered these Azure providers under the specific Azure subscription.
Step 2: In the Azure Portal, click on the “Azure Arc” service or search for “Azure Arc” in the search bar and select the service. In the Azure Arc menu, navigate to the “Machines” section. You can find this under “Infrastructure”. Within the “Machines” section, click on the “Add/Create” button on the top, and select “Add a machine”. In the next window you can choose from three options:
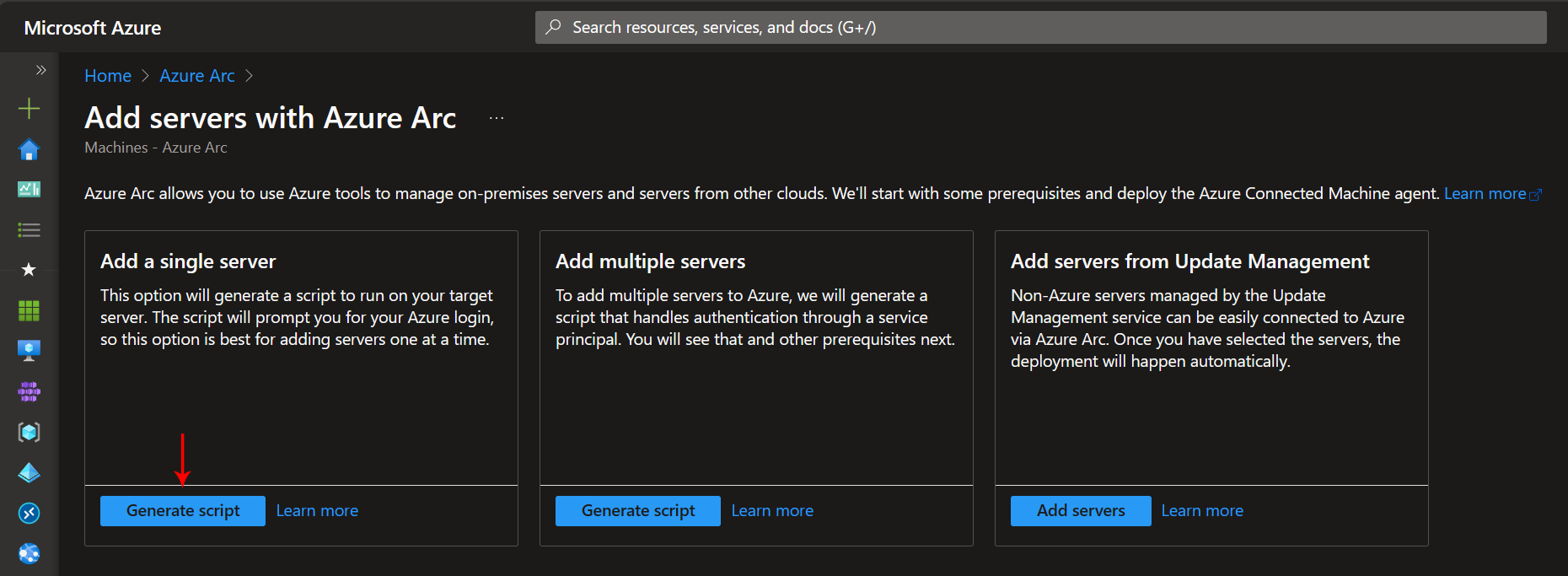
- Add a single server: To add a single server, you can generate a script to run on the target server.
- Add multiple servers: To add multiple servers, you can generate similar scripts for each server individually and run them on the respective servers. This method is suitable for a manageable number of servers.
- Add servers from Update Management: Azure Update Management can help automate the process of adding and managing multiple servers. You can create update deployments that include adding servers to Azure Arc. This is a more streamlined approach for adding servers at scale and ensuring they are consistently managed and updated.
For this guide, we will choose the “Add a single server” option and click the “Generate script” button, as shown in the screenshot below.
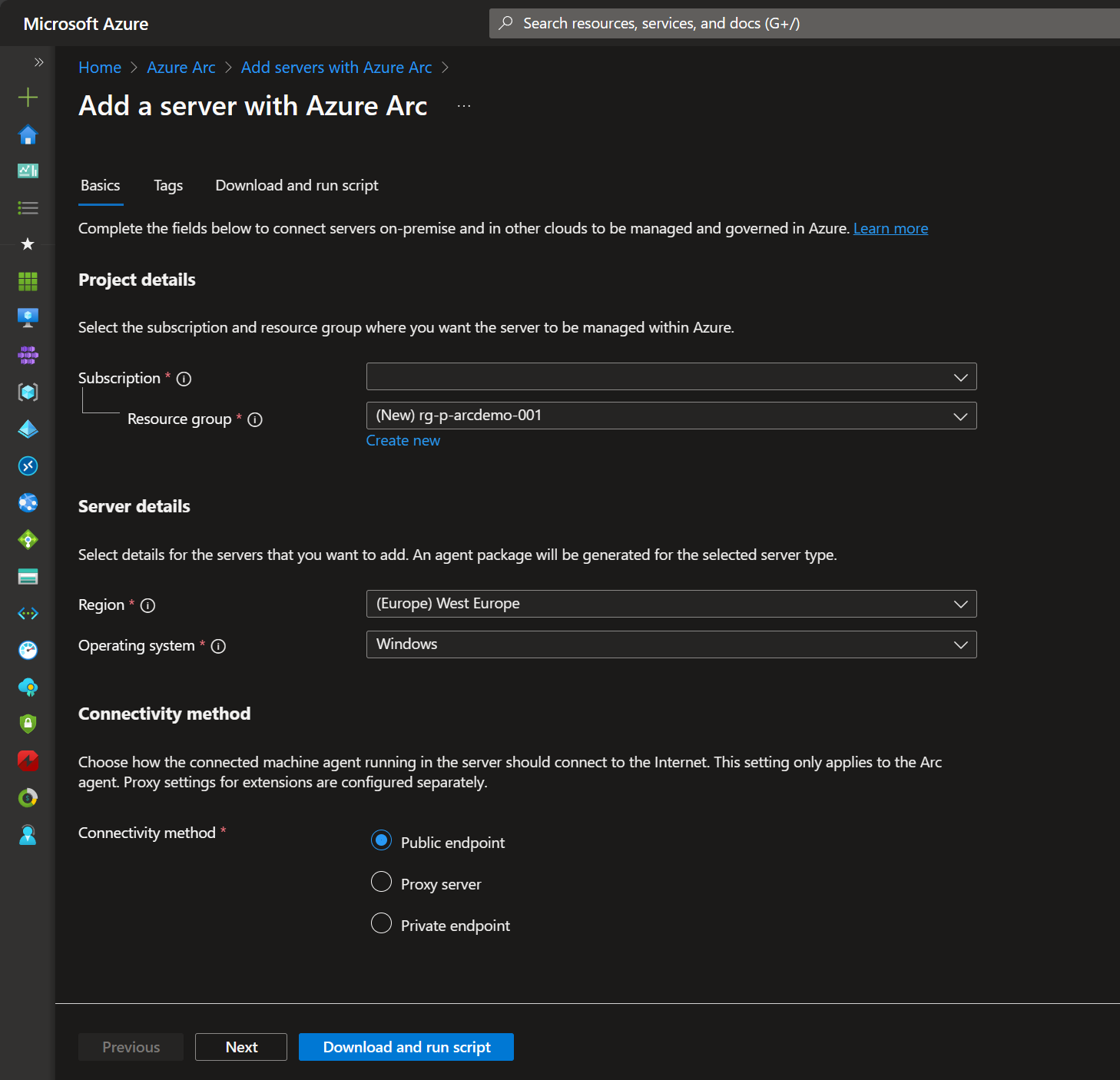
This opens the next window, where we have to provide the required information for the server you want to add. This includes details like the server’s resource group, subscription, region, operating system, and connectivity method. Additionally, you can add Tags if you like for governance/management practices. Press “Download and run script” when you’ve filled in all the necessary fields.
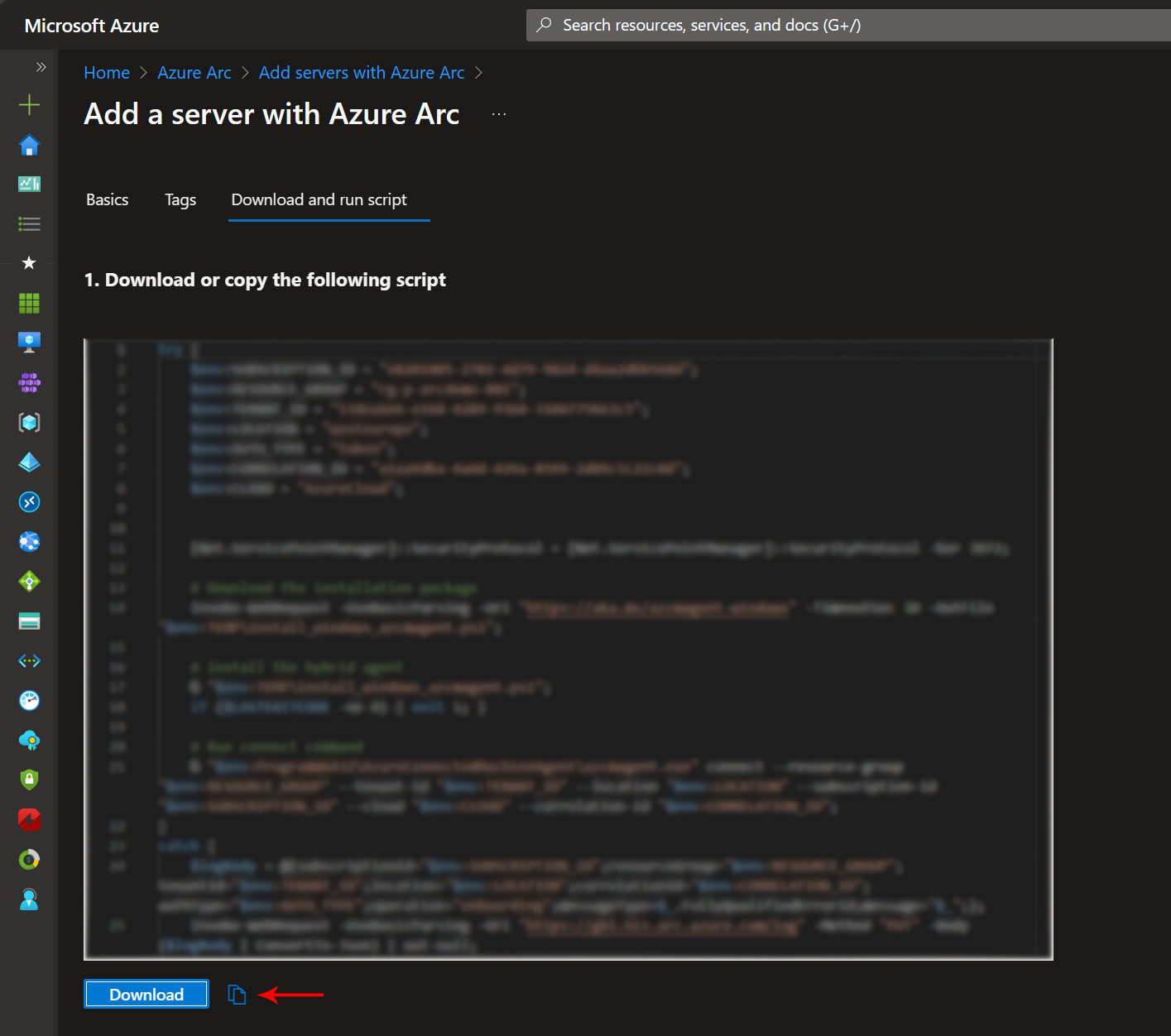
As you configure the server details, the Azure Portal will dynamically generate the PowerShell script that corresponds to your configuration. Review the generated script and ensure it includes all the settings and extensions you want for this server. Press “Download” to download the PowerShell-script file.
Step 3: If you have not completed the previous steps on your Windows Server 2012 (R2) machine, it is important that you move the downloaded script to the Windows Server 2012 (R2) machine that you want to onboard with Azure Arc. Copy the generated PowerShell script and paste it into a PowerShell console, or open the file in PowerShell ISE or IDE of preference, on the server you want to add to Azure Arc. Now, run the script on the server to initiate the registration process. The script will connect your server to Azure Arc and complete the registration process. Part of this process prompts you to login with your Azure (administrative) credentials. After successfully logging in, the process may take a few minutes.
💡 Warning: Make sure the Execution Policy for PowerShell is configured correctly. More information and explanation about PowerShell Execution Policies can be found here.
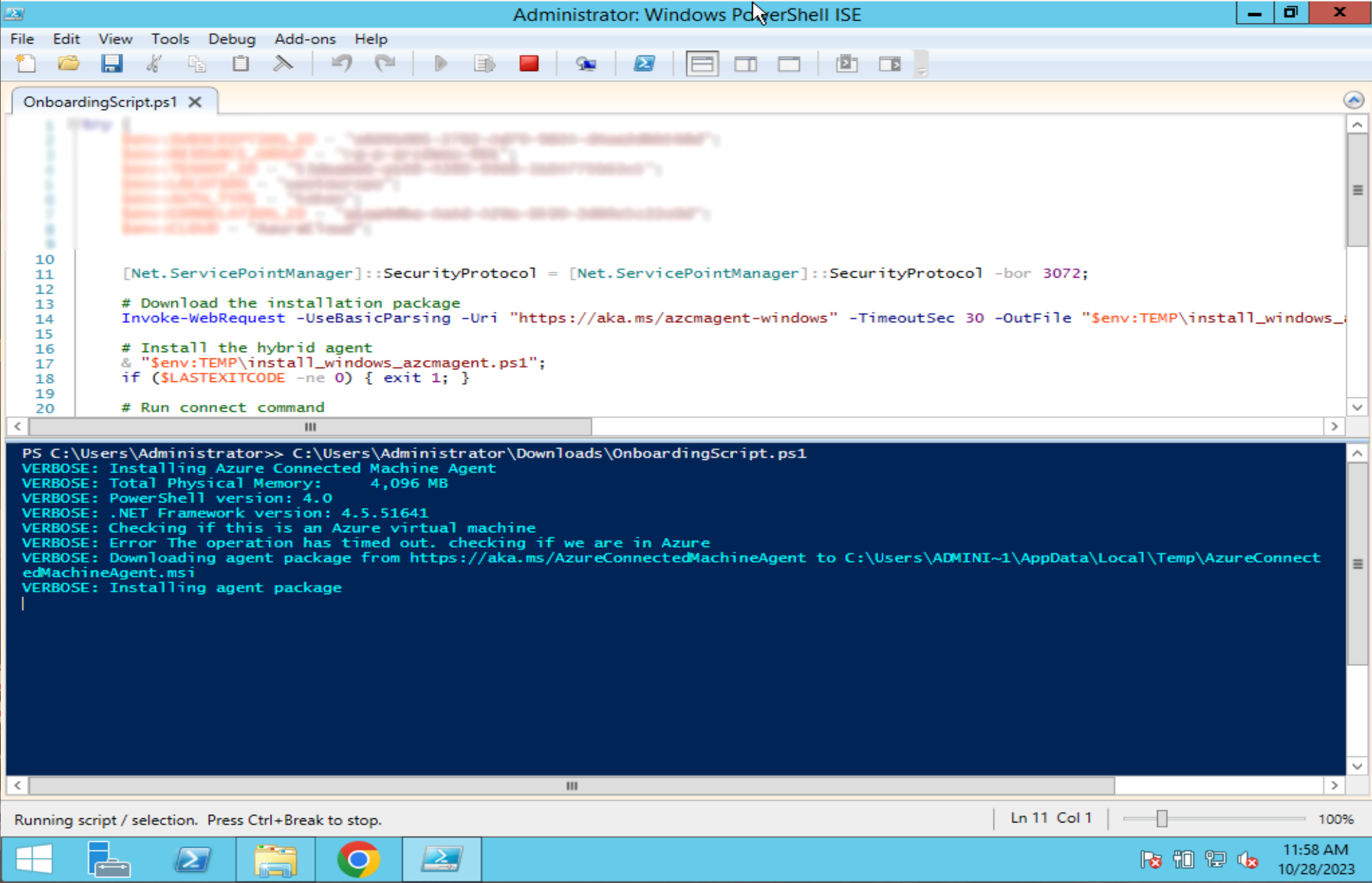
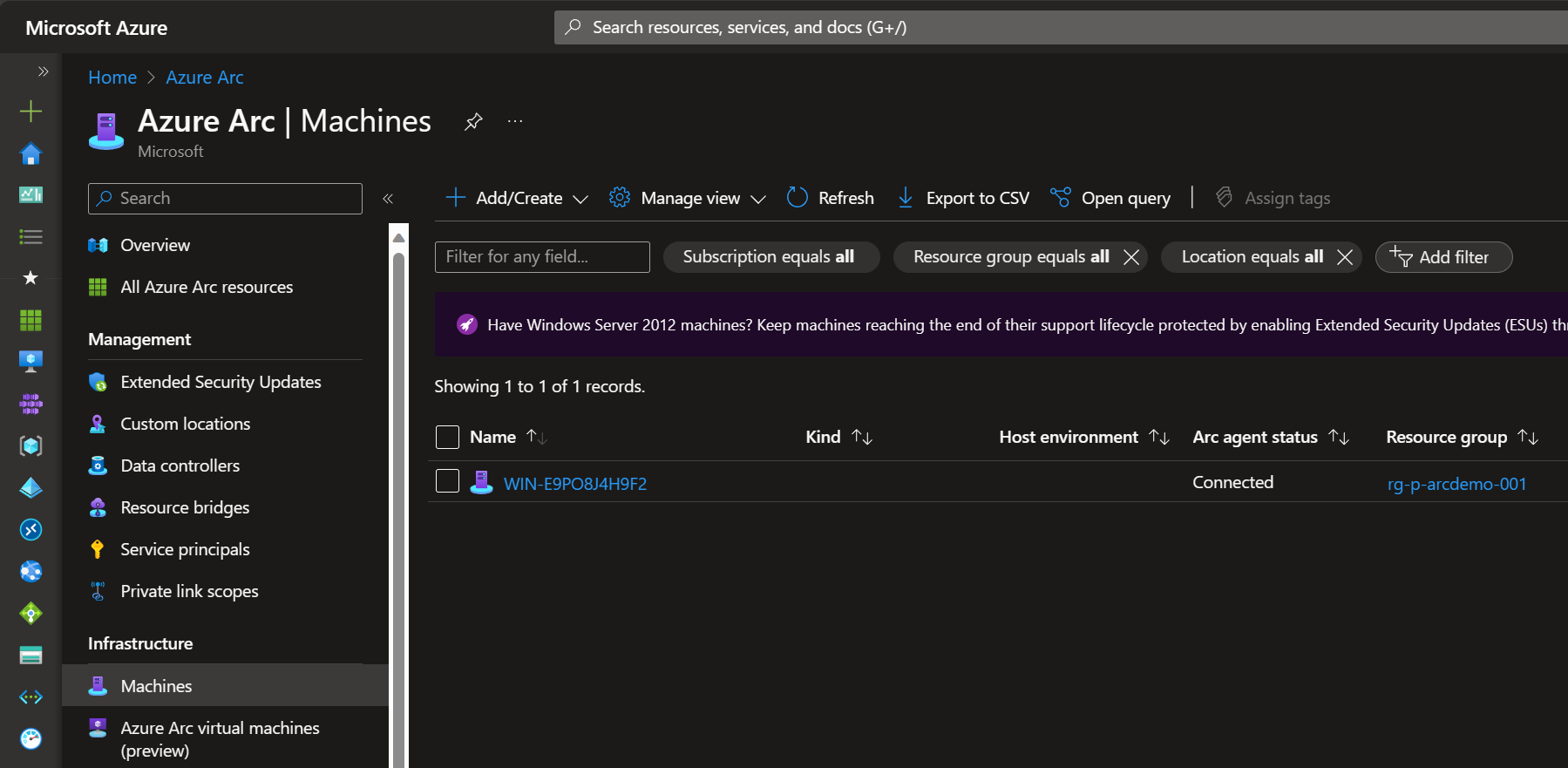
Step 4: Go back to the “Machines” window within the Azure Arc service. Validate that your server is now connected through Azure Arc. The Arc agent status should state it is “Connected”, like the screenshot below.
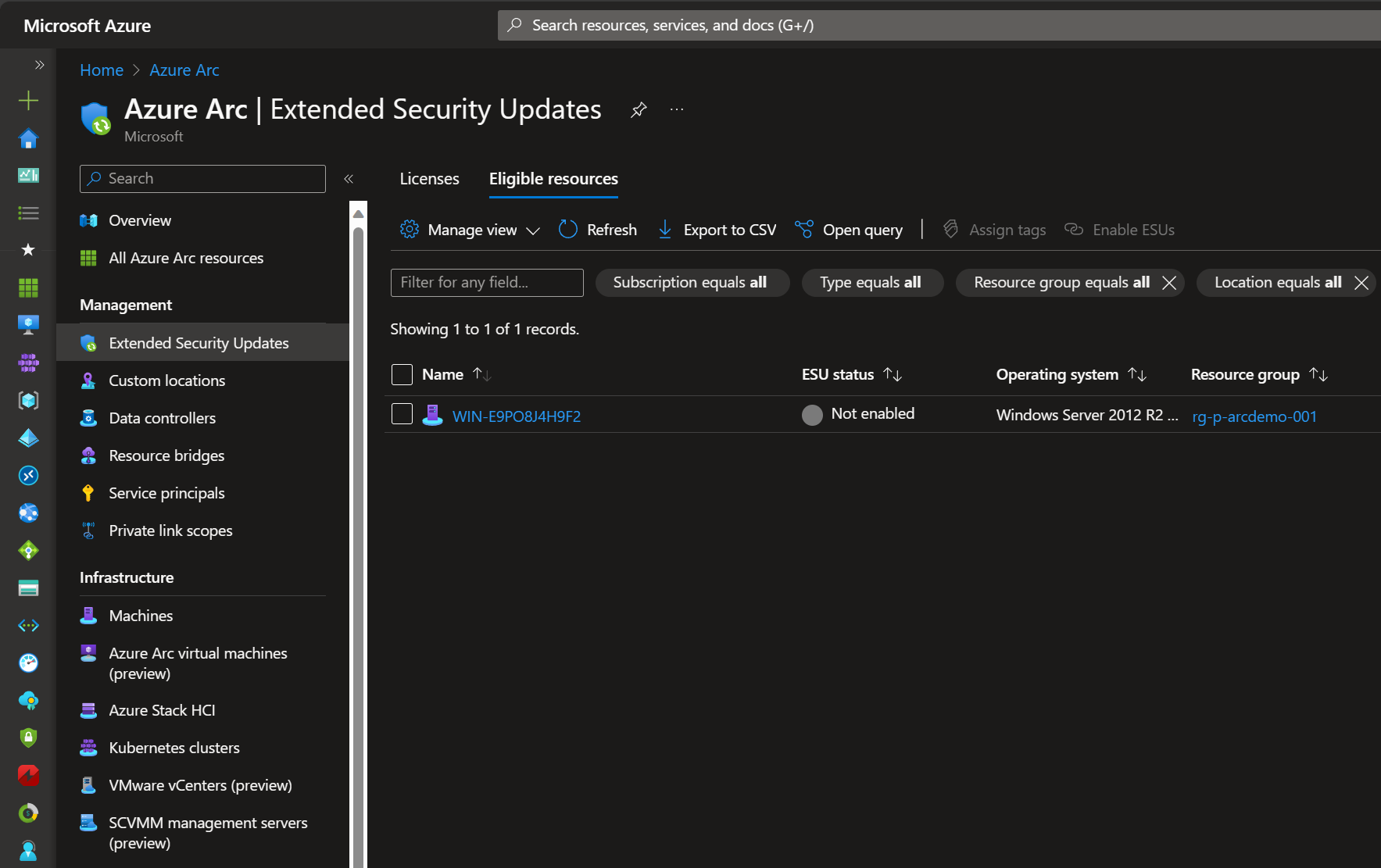
Step 5: In the Azure Portal, within the “Azure Arc” service, navigate to the “Extended Security Updates” section. You can find this under “Management”. Within the “Extended Security Updates” section, click on the “Eligible resources” tab on the top. In this window you should see the recently added Arc-enabled machine, and the “ESU status” shown as “Not enabled”.
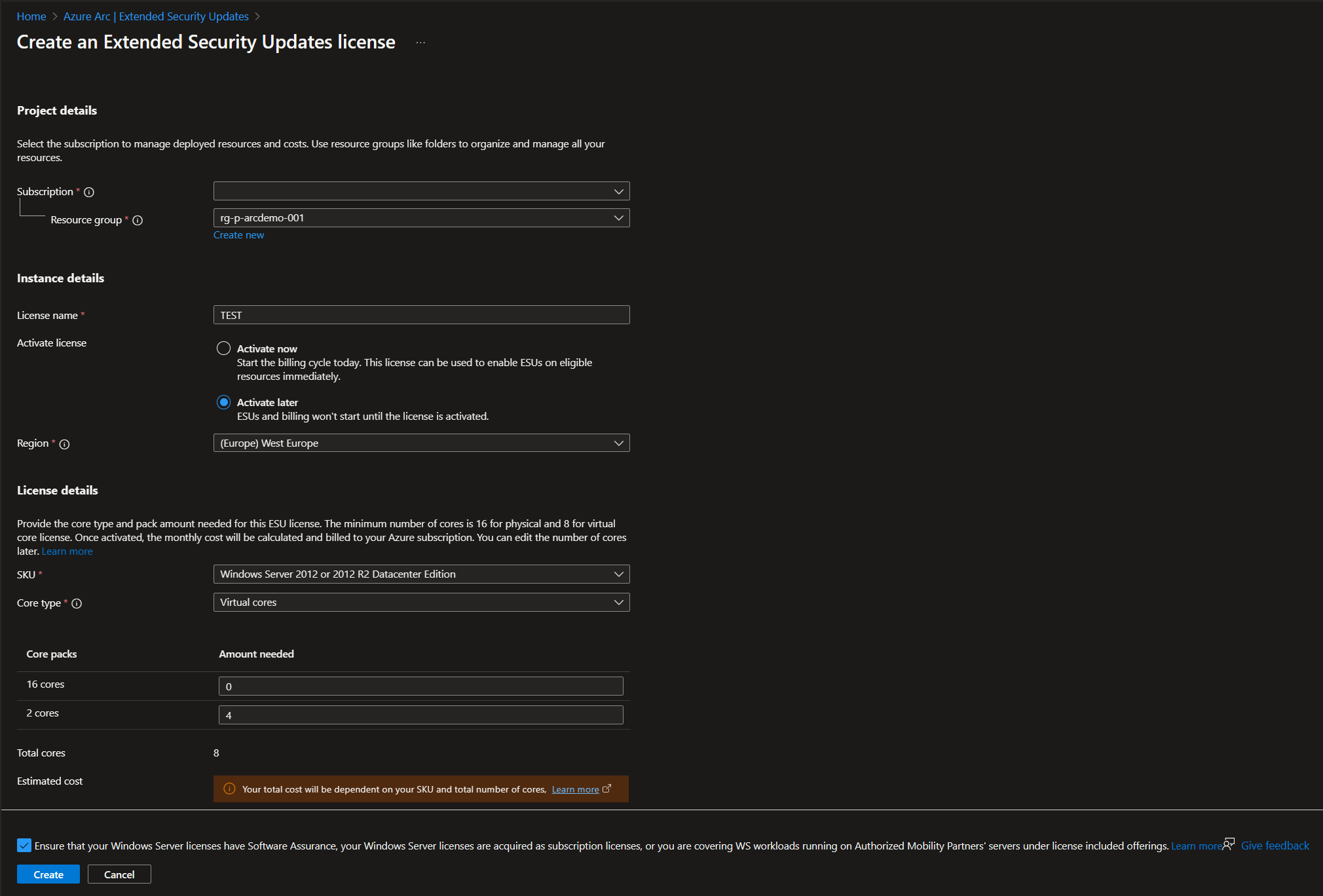
We now have to create a license to enable ESU. Within the “Extended Security Updates” section, click on the “Licenses” tab on the top. Next, click on the “Create” button on top. This opens the next window, where we have to provide the required information for the license you want to create. This includes details like the licenses’ resource group, subscription, name, region, license specific information. As mentioned earlier in this article, you’ll have to choose between the “Physical cores” or “Virtual cores” model. In this guide we’ll choose the “Virtual cores” option, and fill in the minimum required cores needed. Unlike the screenshot below, make sure the license is activated by selecting the “Active now” option, or activate the license before going to the next step. Check the box next to the license conditions and click “Create”.
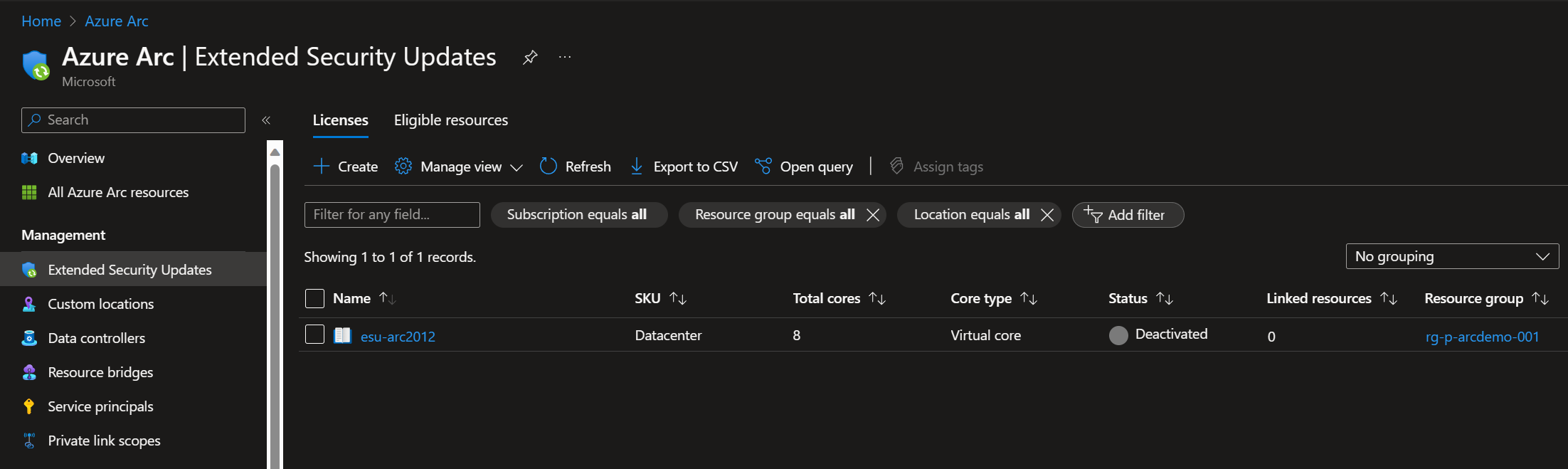
After a few seconds the license is created, like the screenshot below.
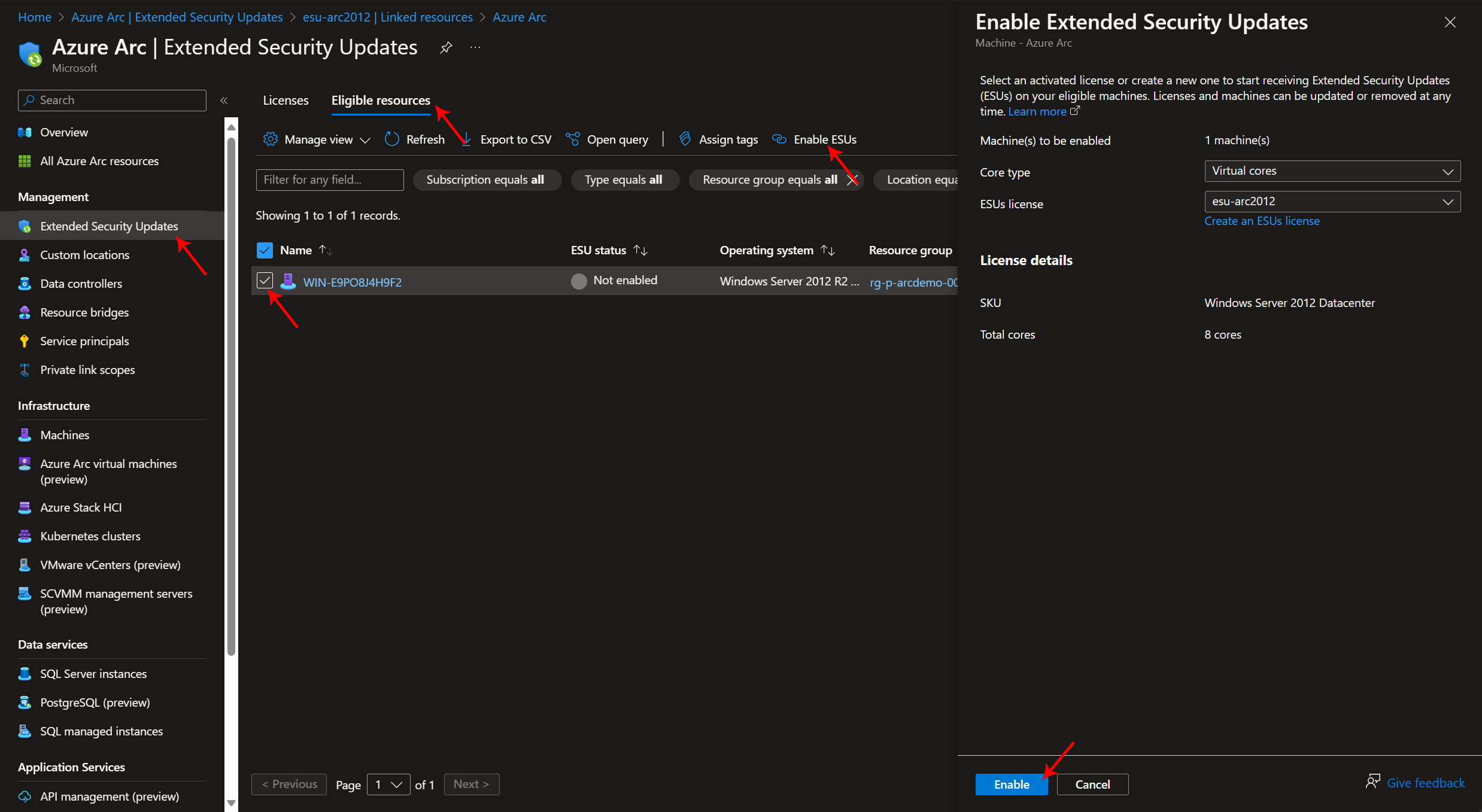
Step 6: Now, the next and final step is to enable ESU on our Arc-enabled VM. Within the “Extended Security Updates” section, click on the “Eligible resources” tab on the top. Select our earlier created Arc-enabled VM resource by checking the box left to it, and click the “Enable ESUs” button. The “Enable Extended Security Updates” configuration window will show on the right. In this window, select the “Core type” equal to the license we just created in the previous step, and for “ESUs license” select the license you just created. Lastly, click on the “Enable” button.
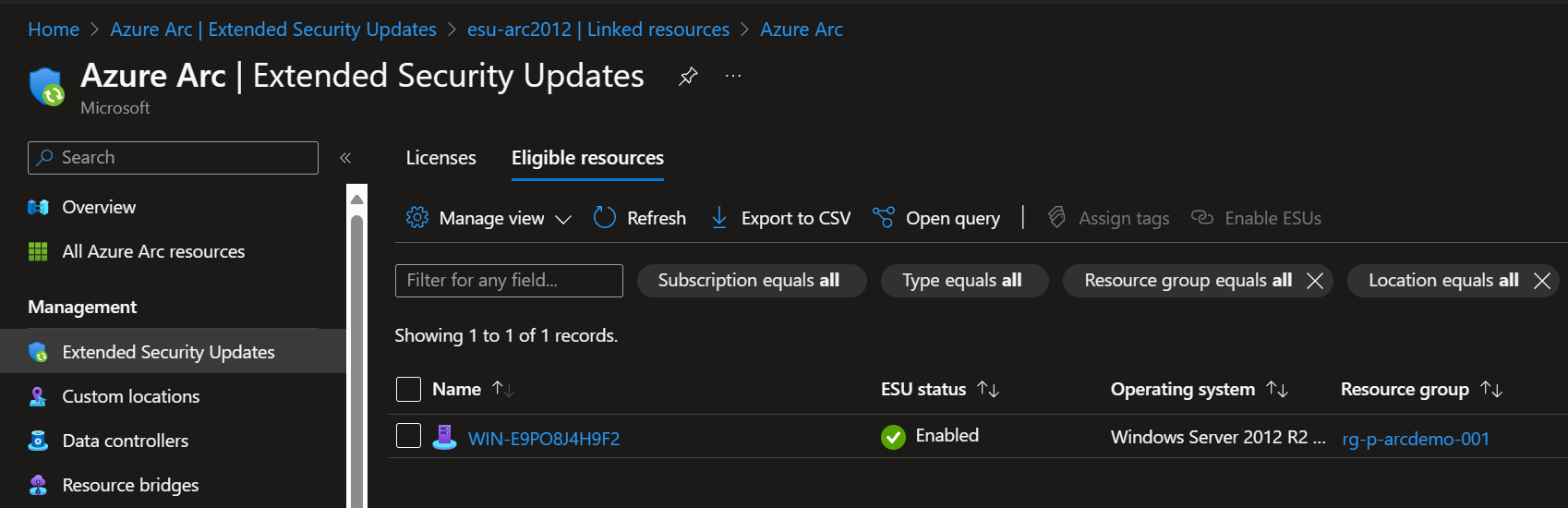
After a few seconds, ESU is successfully enabled on the Arc-enabled VM, as shown in the screenshot below. Congratulations! You’ve completed all the steps to deploy ESU on an Arc-enabled VM. For completeness, check the Arc-enabled VM resource and the license resource in the resource group you specified.
If desired, you can now delete the Arc-enabled VM resource and license so that no further costs are incurred.
What’s Next?
Chances are you don’t want to bother with stretching the lifecycle of your outdated legacy systems and their operating systems, but you are forced to do so due to time, cost, compliance or compatibility reasons. An obvious next step is to upgrade your workload(s) to a newer and supported operating system, or even modernize to a PaaS or SaaS service. Whatever your strategy and ambition is, ESUs through Azure Arc buy you enough time to say goodbye to your legacy systems and their operating systems, while the Pay-as-you-Go model allows you to terminate the ESU immediately when you are ready modernizing your estate.
Another next step could be to make more use of Azure services. If this is your first introduction to Azure, your Azure Arc-enabled VMs are the perfect opportunity to familiarize yourself with what Azure has to offer. Attractive initial services to explore include Azure Update Manager, Azure Automation Change Tracking and Inventory, and Azure Policy Guest Configuration.
To learn more about the topics that were covered in this blog article, refer to the links below:
- Extended Security Updates for SQL Server and Windows Server | Microsoft
- New options for Windows Server 2012/R2 end of support from Azure - Microsoft Windows Server Blog
- How to get Extended Security Updates (ESU) for Windows Server 2008, 2008 R2, 2012, and 2012 R2 | Microsoft Learn
- Connect Windows Server machines to Azure through Azure Arc Setup - Azure Arc | Microsoft Learn
Thank you for taking the time to go through this post and making it to the end. Stay tuned because we’ll keep continuing providing more content on topics like these in the future.
Author: Rolf Schutten
Posted on: October 30, 2023